ADVANCES IN MATHEMATICAL ,PHYSICAL AND CHEMICAL SCIENCES
B.sc computers-2
1. What is Number System? Explain various types of Number System?
Number system refers to a set of symbols and rules used to represent
and manipulate numbers.
In computers, numbers
are represented using different number systems, such as binary,
octal, and hexadecimal.
a. Binary Number System:
●
The binary number system uses only two symbols,
0 and 1.
●
It is the most fundamental number system used in computers
because it directly
corresponds to the on and off states of electronic switches.
●
Each digit in a binary number is called a bit (short for binary
digit), and a group of 8 bits is called a byte.
●
Binary numbers are often used in computer
hardware, programming, and digital communication systems.
b. Octal Number System:
●
The octal number system uses eight symbols, 0 to 7. Each digit
in an octal number represents
a power of 8.
●
Octal numbers
are commonly used in computer
programming, particularly when dealing with permissions or file systems.
●
Octal numbers
are shorter than binary numbers
and provide a convenient representation for grouping bits.
c.
Hexadecimal Number
System:
●
The hexadecimal number system uses sixteen symbols,
0 to 9 and A to F, where A represents 10, B represents 11, and so on, up to F representing 15.
●
Each digit in a hexadecimal number represents a power of 16. Hexadecimal numbers are often used in computer programming, especially when dealing with memory addresses, colors, and binary data.
●
Hexadecimal numbers provide a more compact representation compared to binary
or octal numbers.
Applications of Number Systems in Computers:
-
Binary numbers
are used in computer hardware
to represent digital
signals and perform
logical operations.
-
Octal numbers
are used in file systems
to represent permissions and file attributes.
-
Hexadecimal numbers
are used in programming to represent memory
addresses, machine code instructions, and data structures.
-
All number
systems are used in data representation, data storage, and data manipulation in computer
systems.
-
Converting between number systems is essential
for understanding and troubleshooting computer
systems.
-
Number systems
are also used in cryptography, error detection and correction, and other areas of computer
science.
Sample Problem: Convert the decimal number 85 to binary.
Steps:
1.
Start with the decimal number.
2.
Divide the number by 2.
3.
Write down the remainder
(0 or 1).
4.
Continue dividing the quotient from the previous step by 2 until the quotient becomes
0.
5.
Write down the remainders in reverse order to get the binary
equivalent.
Solution:
- 85 divided by 2 is 42 with a remainder
of 1.
-
42 divided by 2 is 21 with a remainder of 0.
-
21 divided by 2 is 10 with a remainder of 1.
-
10 divided by 2 is 5 with a remainder of 0.
-
5 divided by 2 is 2 with a remainder of 1.
-
2 divided by 2 is 1 with a remainder of 0.
-
1 divided by 2 is 0 with a remainder of 1.
Writing the remainders in reverse order: 1010101. So, the binary
equivalent of decimal
85 is 1010101.
Decimal to Hexadecimal Conversion:
Sample Problem: Convert the decimal
number 189 to hexadecimal.
Steps:
1.
Start with the decimal number.
2.
Divide the number by 16.
3.
Write down the remainder
(0 to 15), replacing 10 with 'A', 11 with 'B', and so on.
4.
Continue dividing the quotient
from the previous step by 16 until the quotient becomes
0.
5.
Write down the remainders
in reverse order to get the hexadecimal equivalent.
Solution:
- 189 divided by 16 is 11 with a remainder
of 13 (which is 'D' in hexadecimal).
- 11 divided
by 16 is 0 with a remainder
of 11 (which is 'B' in hexadecimal).
The remainders in reverse order are BD.
Binary to Decimal Conversion:
Sample Problem: Convert the binary number 110110 to decimal.
Steps:
1.
Start with the binary number.
2.
Write down the binary digits.
3.
Assign each binary digit a positional value: 2^0, 2^1, 2^2, and so on, from right to left.
4.
Multiply each binary digit by its corresponding positional value.
5.
Sum up the results
to get the decimal equivalent.
Solution:
- Binary: 110110
- 0 * 2^0 = 0
- 1 * 2^1 = 2
- 1 * 2^2 = 4
- 0 * 2^3 = 0
- 1 * 2^4 = 16
- 1 * 2^5 = 32
Adding these values together: 0 + 2 + 4 + 0 + 16 + 32 = 54. So, the decimal equivalent of the binary number 110110 is 54. Hexadecimal to Binary Conversion:
Sample Problem: Convert the hexadecimal number 1A3 to binary.
Steps:
1.
Start with the hexadecimal number.
2.
Write down the hexadecimal digits.
3.
Convert each hexadecimal digit to its 4-bit binary
equivalent.
4.
Concatenate the binary equivalents of the hexadecimal digits to get the binary representation.
Solution:
- Hexadecimal: 1A3
-
1 in hexadecimal is 0001 in binary.
-
A in hexadecimal is 1010 in binary.
-
3 in hexadecimal is 0011 in binary.
Concatenating these binary
values: 000110100011.
So, the binary equivalent of the hexadecimal number 1A3 is 000110100011.
72. Explain
about Error detection
and correction
Error detection and correction are techniques used in data communication and storage to ensure data integrity and reliability.
These methods help detect and, in some cases, correct
errors that may occur during data transmission or storage, thereby improving the overall
quality and accuracy
of the data.
Error
Detection:
Error detection is the process of identifying errors in transmitted or stored data. When data is transmitted over a communication channel or stored
in a medium (such as a hard disk or memory), it is susceptible to errors due to noise, interference, or other factors.
Error detection methods involve adding extra bits to the original data, known as redundancy, to enable the receiver to identify if any errors have occurred.
Common
error detection techniques include:
1.
Parity Check: Parity check is a simple error detection technique
used to ensure data integrity
in digital systems.
It involves adding an extra bit, called the parity bit, to a group of data bits. The parity bit is chosen in such a way that the total number of bits with a value of 1 (or 0, depending
on the type of parity used) in the data, including the parity
bit, is either
even or odd.
●
Even Parity: The parity bit is set to make the total
number of 1s (including the parity bit) even. If the data has an odd number of 1s, the parity bit is set to 1, making the total even.
●
Odd Parity: The parity bit is set to make the total number of 1s (including
the parity bit) odd. If the data has an even number of 1s, the parity bit is set to 1, making the total odd.
During data transmission, the sender calculates the parity bit and includes
it with the data. The receiver recalculates the parity bit based on the received data and checks if it matches the received
parity bit. If they match,
it indicates that no error has occurred
during transmission. However, if they don't match, an error is detected.
Parity check can detect single-bit errors, where only one bit in the data has changed. However,
it cannot correct errors or detect multiple
errors.
2. Cyclic
Redundancy Check (CRC): CRC is a more sophisticated error detection technique commonly used in
data communication and storage. It involves generating a checksum or code from the
data using polynomial division. The resulting code is appended
to the data before transmission.
The receiver also performs the same polynomial
division on the received data (including the code) and compares the calculated code with the received code. If they match, it indicates that no errors have occurred
during transmission. However,
if they don't match, an error is detected.
CRC provides a higher level of error detection capability compared to simple parity check. It can detect a wider range of errors, including burst errors where multiple consecutive bits are corrupted. While CRC can detect errors,
it doesn't correct
them. Instead, it relies on retransmission or higher-level error correction techniques to recover from errors.
CRC is widely used in network protocols, storage systems, and other applications where data integrity is critical.
Error Correction:
Error correction goes beyond error detection by not only identifying errors but also attempting to correct them automatically. This is especially useful in scenarios
where data integrity
is crucial, such as in critical
communication systems or storage devices.
Common
error correction techniques include:
- Forward Error Correction (FEC): FEC adds redundant data to the original data, which allows the receiver to correct errors without the need for retransmission. It provides a level of resilience to errors and can recover from a certain number of errors, depending on the coding scheme used.
- Automatic Repeat Request (ARQ): ARQ is a feedback-based error correction method.
The receiver detects
errors and requests
the sender to retransmit the corrupted data. The process
continues until the data is received correctly, or a predefined number of retransmissions is reached.
73.
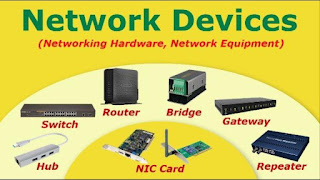
What is a Networking Device? List out the Networking Devices .
A networking device
is any hardware or software
component used to facilitate communication and data exchange
between devices in a computer
network. These devices
help manage, control,
and direct data traffic, enabling
efficient and reliable
data transmission between
connected devices.
1. Repeater:
A repeater is a simple networking device used to amplify and regenerate signals in a network. It operates at the physical layer of the OSI model and is primarily
used to extend the reach of a network by boosting the signal strength
of data transmissions. When data travels over long distances, it may suffer from signal degradation, resulting
in data loss or errors.
Repeaters receive weak signals, amplify
them, and retransmit them to extend the network's coverage.
2. Hub:
A hub is a basic networking device that operates
at the physical layer of the OSI model. It serves as a central connection point for multiple
devices in a network. When a device sends data to a hub, the hub broadcasts the data to all connected
devices. As a result, all devices connected
to the hub receive the data, even if it is intended for a specific device. Hubs are considered legacy devices and are less common in modern networks
due to their limitations in handling network congestion and inefficient use of bandwidth.
3.
Bridge:
A bridge is a networking device that operates
at the data link layer of the OSI model (Layer 2). It connects
two or more network segments
and uses their MAC (Media Access Control)
addresses to selectively forward data between
them. Unlike hubs, bridges filter and forward
data only to the segment where the intended destination device is located,
reducing unnecessary data transmission and minimizing network
collisions. Bridges are used to break up large collision domains and segment
network traffic, which improves network
performance and efficiency.
4. Switch:
A switch is an advanced
networking device that operates at the data link layer (Layer 2) or the network layer (Layer 3) of the OSI model. It is more intelligent than hubs and bridges and has the capability to learn the MAC addresses of connected devices.
Switches use this information to create a MAC address table, enabling them to forward data directly to the appropriate destination device without
broadcasting to all connected devices. This process is known as packet switching, which reduces unnecessary data transmission and collisions. Switches
are the most common devices
used in modern wired Ethernet
networks.
5. Router:
A router is a networking device that operates
at the network layer (Layer 3) of the OSI model. It is used to connect multiple networks
together and make decisions about
how to route data packets
between them based on IP addresses. Routers maintain routing
tables to determine
the best path for data to reach its destination across interconnected networks.
They are essential in connecting different networks, such as the internet, and play a vital role in directing
data traffic efficiently between
networks.
6. Gateway:
A gateway is a device or
software component that connects networks with
different communication protocols or architectures. It serves as an intermediary between different networks
to facilitate data exchange.
Gateways can perform protocol translation, data format conversion, and other necessary tasks to ensure seamless communication between otherwise incompatible networks
4. What are signals
in Computers?Explain in brief about
Analog and digital
signals.
An electrical or electromagnetic quantity
(current, voltage, radio wave, micro wave, etc.) that carries data or information from one system (or network)
to another is called a signal.
Here are some key points about signals and their usage in computers:
1.
Communication: Signals are used for communication between different components of a computer
system
2.
Data Processing: Signals are used to represent and process data in computers.
In digital systems,
data is represented using binary signals, where each bit (0 or 1) represents a specific state
3.
Control: Signals are used for controlling the operation of various hardware components in a computer
system.
4.
Input and Output: Signals are used to interface
with input and output devices in computers. For example, when you press a key on a keyboard, it generates an electrical signal that is sent to the computer,
indicating the specific
key pressed
There are two major types of signals used in a computer they are:
a) Analog
Signals
A signal which is a continuous function
of time and used to carry the information is known as an analog signal. An analog
signal represents a quantity analogous to another quantity,
for example, in case of an analog audio signal, the instantaneous value of signal voltage represents
the pressure of the sound wave.
Analog
signals utilize the properties of medium to convey the information. All the natural signals are the examples
of analog signals.
However, the analog signals are more susceptible to the electronic noise and distortion
which can degrade the quality of the signal.
b) Digital
Signal
A signal that is discrete function of time, i.e. which is not a continuous signal, is known as a digital signal. The digital
signals are represented in the binary form and consist of different values
of voltage
at discrete instants
of time.
Basically, a digital signal represents the data and information as a sequence
of separate values at any given time. The digital signal can only take on one of a finite number
of values.
Difference between Analog and Digital Signal
|
Analog Signal |
Digital Signal |
|
A signal for conveying information which is a continuous function of time
is known as analog signal. |
A signal which is a discrete function
of time, i.e. non-continuous signal,
is known as digital signal. |
|
An analog
signal is typically represented by a sine wave
function. |
The typical representation of a signal
is given by a square wave function. |
|
Analog signals use a continuous range of values to represent the data and information. |
Digital signals use discrete values
(or discontinuous values),
i.e. discrete 0 and 1, to represent the data and information. |
|
The bandwidth of an analog
signal is low. |
The bandwidth of a digital
signal is relatively high. |
|
The analog signals
are more suitable for transmission of
audio, video and other information through the communication channels. |
The digital
signals are suitable
for computing and digital electronic operations such as data storage, etc. |
|
Analog signals
get affected by the electronic noise easily. |
The digital signals
are more stable
and less susceptible to noise than the analog signals. |
|
Analog signals use more power
for data transmission. |
Digital signals use less power
than analog signals for conveying
the same amount of information. |
|
The analog
signals give observational errors. |
The digital
signals do not given observational errors. |
|
The common
examples of analog signals are temperature, current, voltage, voice, pressure, speed, etc. |
The common example of digital signal is the data store in a computer memory. |
Explain
briefly about Transmission data.
- Transmission media is a communication channel that carries the information from the sender to the receiver. Data is transmitted through the electromagnetic signals.
- The main functionality of the transmission media is to carry the information in the form of bits through LAN(Local Area Network).
- It is a physical path between transmitter and receiver in data communication.
- In a copper-based network, the bits in the form of electrical signals.
- In a fibre based network, the bits in the form of light pulses.
- In OSI(Open System Interconnection) phase, transmission media supports the Layer 1. Therefore, it is considered to be as a Layer 1 component.
- The electrical signals can be sent through the copper wire, fibre optics, atmosphere, water, and vacuum.
- The characteristics and quality of data transmission are determined by the characteristics of medium and signal.
- Transmission media is of two types are wired media and wireless media. In wired media, medium characteristics are more important whereas, in wireless media, signal characteristics are more important.
- Different transmission media have different properties such as bandwidth, delay, cost and ease of installation and maintenance.
- The transmission media is available in the lowest layer of the OSI reference model, i.e., Physical layer.
Causes Of Transmission Impairment:
- Attenuation: Attenuation means the loss of energy, i.e., the strength of the signal decreases with increasing the distance which causes the loss of energy.
- Distortion: Distortion occurs when there is a change in the shape of the signal. This type of distortion is examined from different signals having different frequencies. Each frequency component has its own propagation speed, so they reach at a different time which leads to the delay distortion.
- Noise: When data is travelled over a transmission medium, some unwanted signal is added to it which creates the noise.
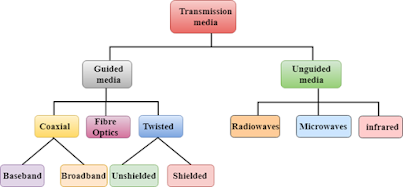
There are primarily two types of transmission media:
1. Guided
Transmission Media (Wired):
Guided transmission media use physical conductors to transmit signals
and data. The signals are confined within
the physical medium,
which provides a defined path for data transmission. Some common types of guided transmission media
include:
- Twisted Pair Cable: Consists of two insulated copper wires twisted
together, commonly used for Ethernet
networks and telephone
lines.
- Coaxial Cable: Contains
a central copper conductor surrounded by an
insulating layer, shield, and outer jacket. Coaxial cables were widely used in traditional cable TV networks and Ethernet
connections.
- Optical Fiber: Uses thin strands of glass or plastic to transmit data as pulses of light. Optical fiber offers high data transfer
rates, low signal
loss, and immunity
to electromagnetic interference.
2. Unguided
Transmission Media (Wireless):
Unguided
transmission media utilize
the air or free space as the medium for transmitting signals.
In wireless communication, data is propagated through the atmosphere in the form of electromagnetic waves. Common types of unguided
transmission media include:
- Radio Waves: Used in wireless communication technologies such as Wi-Fi,
Bluetooth, and radio broadcasting.
- Microwaves: Higher-frequency radio waves employed in microwave communication for point-to-point connections and satellite communication.
- Infrared Waves: Used in
short-range wireless communication, such as
infrared data transfer between devices like remote controls and IrDA (Infrared Data Association) connections.
Each type of transmission medium has its advantages and limitations. Wired media generally
provide higher data rates and more reliable
connections but are limited by physical constraints and require proper installation. Wireless media offer mobility and flexibility but can be affected by interference and have limitations in terms of range and data rates.





Comments
Post a Comment